Beyond the Breach: Understanding the True Damage of Data Security Failures
June 7, 2024
Building a Strong Cyber Defense: The Importance of Security Policies
June 11, 2024Why Security Risk Assessments are Essential for Your Cyber Defense Strategy
In our modern digital landscape, cybersecurity is more critical than ever. With the increasing frequency and danger of cyber threats, organizations must adopt comprehensive security measures to protect their sensitive data and systems. One essential component of an effective cybersecurity strategy is the security risk assessment (SRA). This process helps organizations identify, evaluate, and mitigate potential security risks. In this blog, we’ll explore the role of security risk assessments in cybersecurity strategy and how Athreon’s SRA services can help safeguard your organization.
Understanding Security Risk Assessments
A security risk assessment systematically identifies potential threats and vulnerabilities within an organization’s IT infrastructure. The primary goal is to understand the risks associated with the organization’s assets and to develop strategies to mitigate these risks. Key elements of a security risk assessment include:
- Asset Identification: Cataloging all critical assets within the organization, including hardware, software, data, and personnel.
- Threat Identification: Identifying potential threats that could compromise the security of these assets. Threats can be internal (e.g., disgruntled employees) or external (e.g., hackers, natural disasters).
- Vulnerability Assessment: Analyzing the organization’s systems and processes to identify weaknesses that threats could exploit.
- Risk Analysis: Evaluating the probability and impact of each identified risk.
- Risk Evaluation: Prioritizing risks based on their significance and determining appropriate risk treatment options.
The Importance of Security Risk Assessments
Security risk assessments are crucial for several reasons:
Enhancing Overall Security Posture
Organizations can notably enhance their overall security posture by identifying and addressing potential security risks. This proactive approach helps prevent security incidents before they happen, reducing the chances of data breaches and other cyber threats.
Identifying and Prioritizing Risks
Security risk assessments help organizations identify and prioritize risks based on their potential impact. This empowers organizations to allocate their resources effectively and address the most critical risks first.
Ensuring Compliance with Regulations and Standards
Many industries are subject to strict mandates regarding data protection and cybersecurity. Conducting regular security risk assessments helps organizations ensure compliance with these regulations, avoiding costly fines and reputational damage.
Facilitating Informed Decision-Making
Security risk assessments provide valuable insights into an organization’s security landscape. This information enables leaders to make informed choices about security investments and strategies, ensuring that resources are used efficiently.
Reducing the Potential Impact of Security Incidents
Organizations can reduce the potential damage of security incidents by identifying vulnerabilities and implementing appropriate mitigation measures. This helps minimize downtime, financial losses, and damage to the organization’s reputation.
Steps to Conduct a Security Risk Assessment
Conducting a security risk assessment involves several key steps:
- Preparation
- Establish the assessment’s context and scope.
- Define roles and responsibilities for the assessment team.
- Asset Identification
- Catalog all critical assets within the organization.
- Assess the value and importance of each asset.
- Threat Identification
- Identify potential threats to each asset.
- Consider both internal and external threats.
- Vulnerability Assessment
- Analyze systems and processes to identify weaknesses.
- Use tools and techniques to uncover vulnerabilities.
- Risk Analysis
- Evaluate the probability and impact of all identified risks.
- Combine threat and vulnerability data to assess overall risk.
- Risk Evaluation
- Prioritize risks based on their significance.
- Determine appropriate risk treatment options, such as mitigation, acceptance, transfer, or avoidance.
- Documentation and Reporting
- Create a comprehensive risk assessment report.
- Communicate findings to stakeholders and develop an action plan.
Integrating Risk Assessments into Cybersecurity Strategy
To maximize the effectiveness of security risk assessments, organizations should integrate them into their overall cybersecurity strategy. This involves:
Continuous Monitoring and Regular Assessments
Cyber threats are always evolving, making it essential to conduct regular security risk assessments. Continuous monitoring helps organizations stay ahead of emerging threats and adapt their security measures accordingly.
Aligning Risk Assessments with Business Objectives
Security risk assessments should align with the organization’s business objectives and goals. This ensures that security measures support the organization’s mission and do not hinder business operations.
Incorporating Risk Assessment Findings into Policy Development
Findings from security risk assessments should inform the development of security policies and procedures. This helps create a robust security framework that addresses identified risks and vulnerabilities.
Ensuring Incident Response Plans are Informed by Risk Assessments
Incident response plans should be based on the findings of security risk assessments. This ensures that the organization is ready to respond intelligently to security incidents and minimize their impact.
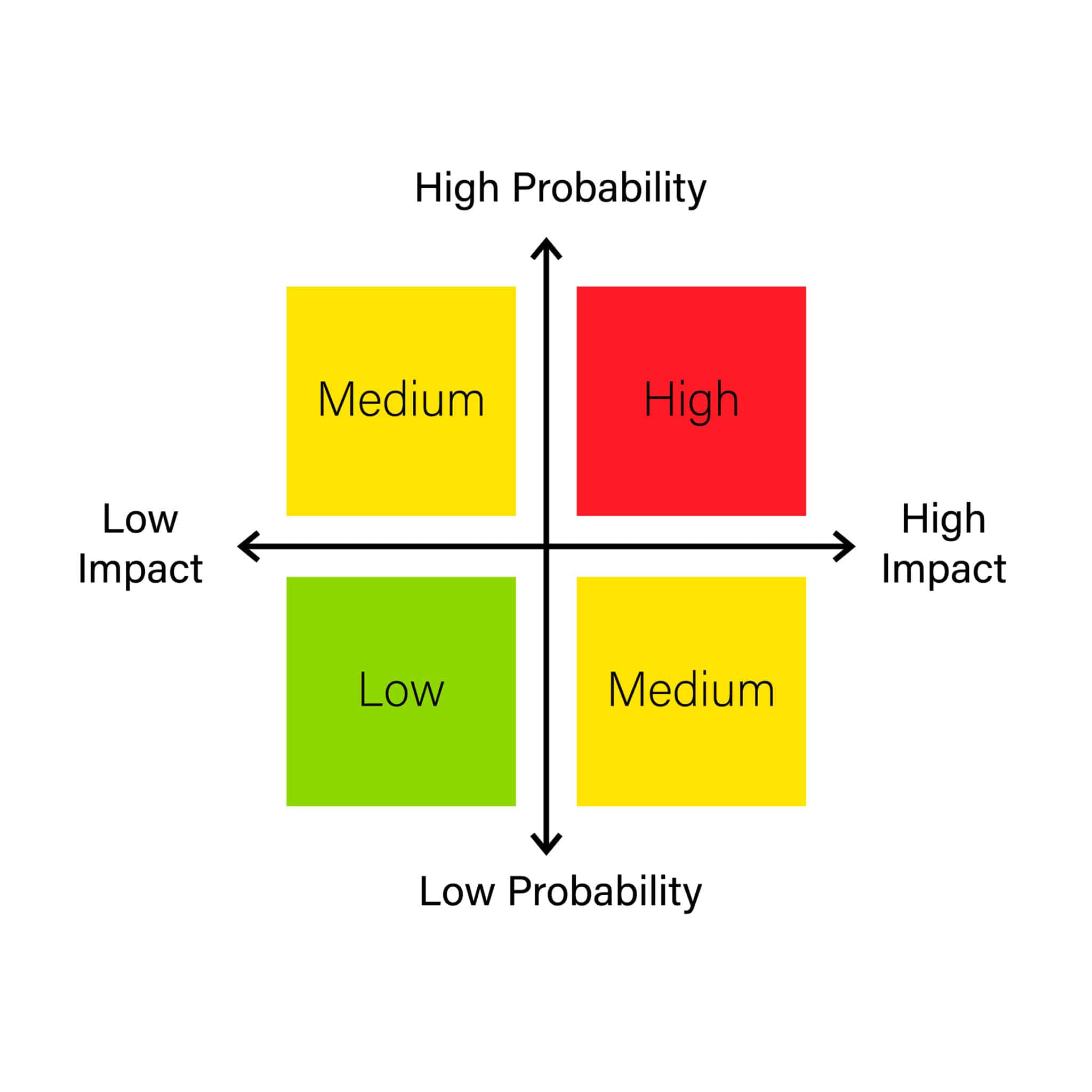
Benefits of Regular Security Risk Assessments
Regular security risk assessments offer numerous benefits:
Proactive Threat Mitigation
By identifying and addressing potential threats proactively, businesses can prevent security incidents before they occur.
Improved Resource Allocation
Risk assessments help organizations allocate resources more effectively, focusing on the most critical risks first.
Enhanced Security Awareness Among Employees
Conducting regular risk assessments helps raise employees’ awareness of security risks, fostering a culture of security within the organization.
Strengthened Trust with Clients and Partners
Demonstrating a commitment to security through regular risk assessments helps build trust with clients and partners, enhancing the organization’s reputation.
Best Practices for Effective Security Risk Assessments
To conduct effective security risk assessments, organizations should follow these best practices:
- Stay Aware of the Latest Threats and Vulnerabilities: Routinely review threat intelligence reports and security advisories to remain informed about new threats and vulnerabilities.
- Involve Cross-Functional Teams: Engage stakeholders from different departments to comprehensively assess the organization’s security landscape.
- Leverage Advanced Tools and Technologies: Use automated tools and technologies to simplify the risk assessment process and identify vulnerabilities more efficiently.
- Regularly Review and Update Risk Assessments: Conduct regular assessments to ensure the organization’s security measures remain effective against evolving threats.
Master Security Risk Assessments with Athreon
Security risk assessments play a critical role in an effective cybersecurity strategy. Organizations can enhance their security posture, ensure compliance with regulations, and make informed decisions about security investments by identifying, evaluating, and mitigating potential security risks. Regular risk assessments also help reduce the potential impact of security incidents and build trust with clients and partners.
At Athreon, we understand the importance of security risk assessments in protecting your organization’s sensitive data and systems. Our comprehensive SRA services help you identify and address potential security risks, ensuring your organization remains secure and resilient against cyber threats. Contact us today to learn more about how our SRA services can benefit your organization.
Protect Your Business
Ready to enhance your organization’s cybersecurity strategy? Contact Athreon for a free consultation or to schedule a security risk assessment. Explore our website for more information and access to valuable resources and tools for conducting security risk assessments.