Defend Your Business Against Malware: What You Need to Know
In our digital age, malware poses a major threat to businesses of all sizes. It is crucial to understand what malware is, how it operates, and the steps you can take to protect your business. This blog will provide an in-depth look at malware, its various forms, and essential preventative measures to safeguard your business.
Types of Malware
Viruses
Viruses are harmful software that attach themselves to legitimate files and programs. Once activated, they replicate and spread to other files and systems. Viruses can corrupt or delete data and slow down system performance. A notable example is the ILOVEYOU virus, which caused widespread damage in the early 2000s.
Worms
Unlike viruses, worms do not need to link to files to spread. They can propagate independently across networks, exploiting vulnerabilities in operating systems or software. The SQL Slammer worm is an infamous case, causing significant disruptions by rapidly spreading across the internet in 2003.
Trojans
Trojans mimic legitimate software, tricking users into installing them. Once installed, they can create backdoors, allowing cybercriminals to access and control systems remotely. The Zeus Trojan is a well-known example, used primarily to steal banking information.
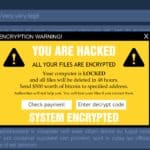
Ransomware
Ransomware encrypts a victim’s data and demands payment for the decryption key. It has become a lucrative business for cybercriminals, with high-profile attacks like WannaCry affecting organizations worldwide. The financial and operational impacts of ransomware can be devastating.
Spyware and Adware
Spyware secretly monitors user activity, capturing sensitive information such as passwords and credit card numbers. Adware, while less harmful, bombards users with unwanted advertisements. Both can compromise data security and reduce productivity.
Rootkits
Rootkits hide malicious activity on a system, making detection and removal challenging. They often allow attackers to maintain persistent access to compromised systems, posing long-term security risks.
How Malware Infects Systems
Common Vectors of Infection
- Phishing Emails: Attackers send emails that appear legitimate, misleading users into clicking malicious links or downloading infected attachments.
- Malicious Downloads: Downloading software from untrusted sources can introduce malware.
- Infected Websites: Visiting compromised websites can result in drive-by downloads, where malware gets installed without the user’s knowledge.
- USB Drives and External Devices: Connecting infected USB drives or other external devices can introduce malware to your system.
Social Engineering Techniques
Cybercriminals often exploit human psychology to bypass technical defenses. Techniques include:
- Pretexting: Creating a fabricated scenario to obtain sensitive information.
- Baiting: Offering something enticing to lure users into a trap.
- Quid Pro Quo: Promising a benefit in exchange for information or access.
Consequences of a Malware Infection
Financial Losses
Malware attacks can result in devastating financial losses. Direct costs include ransom payments and recovery expenses, while indirect costs encompass downtime and lost productivity.
Data Breaches and Loss of Sensitive Information
Malware can lead to data breaches, exposing sensitive business information and customer data. This can have dire consequences, including identity theft and financial fraud.
Reputational Damage
A malware infection can erode customer trust and damage your business’s reputation. Recovering from reputational damage can be difficult and all-consuming.
Legal and Regulatory Consequences
Companies must comply with data protection laws. A malware-induced data breach can result in hefty fines and legal actions, further compounding the financial impact.

Preventative Measures
Employee Training and Awareness
Employees are often the first line of defense against malware. Regular cybersecurity training can help them recognize and avoid phishing and social engineering attacks. Educate your staff on best practices, such as not clicking on suspicious links and verifying email sources.
Robust Security Software
Invest in comprehensive security solutions, including antivirus and anti-malware software. Firewalls and intrusion detection systems can offer further layers of protection, blocking unauthorized access and monitoring network activity.
Regular Updates and Patching
Keeping software and systems up-to-date is crucial. Cybercriminals often exploit known vulnerabilities, so applying patches and updates promptly can mitigate these risks.
Data Backup Strategies
Regularly back up your data and store backups securely. Reliable backups can enable you to restore your systems without paying the ransom in a ransomware attack. Implementing a recovery plan can minimize downtime and data loss.
Access Controls and Privilege Management
Adopt the principle of least privilege, ensuring employees have access only to the information necessary for their roles. Regularly review user access permissions to prevent unauthorized access and reduce the potential attack surface.
What to Do If You Are Infected
Immediate Steps to Take
If you suspect a malware infection, identify the impacted computers to prevent further spread. Disconnect them from the network and shut them down if necessary. Contact cybersecurity professionals for assistance in containing and eradicating the malware.
Recovery and Restoration
Removing malware and restoring systems can be complex. Use trustworthy antivirus and anti-malware tools to scan and clean your systems. Once cleaned, restore data from backups. Analyze the incident to identify weaknesses in your security measures and improve your defenses.
Protect Your Business With Athreon
Understanding the various types of malware and how they can affect your business is the first step in protecting your organization. Implementing robust security measures, educating your employees, and staying vigilant can notably limit the risk of a malware infection. By being proactive, you can safeguard your business’s data, reputation, and financial stability.
Contact Athreon Today
Is your business prepared to defend against malware threats? Review your current cybersecurity measures and take action to fortify your defenses. Athreon offers comprehensive cybersecurity training and consulting services to help you stay ahead of cyber risks. Contact us today to learn how we can support your cybersecurity needs and ensure your business remains secure.
Contact Athreon for more information and additional resources on malware and cybersecurity. With Athreon’s expert guidance, you can protect your company from the increasingly-tricky landscape of cyber threats.