Police Transcription Services Can Help Agencies Emphasize Officer Well-Being
February 19, 2021
Medical Scribes—Are On-site or Virtual Scribes Better?
March 8, 2021Are we playing dice with EMR security?
EMR security echoes throughout every healthcare IT annual budget forecast, infrastructure planning, and hospital department nationwide. It keeps the technologists on their toes and healthcare industry leaders awake at night. In the advent of cyberattacks getting smarter and strategically more versed day by day, more vulnerabilities are being identified and exploited (see Figure 1). Information Technology and human practice—the how and what we do with personally identifiable information (PII) using technology—are at center stage.
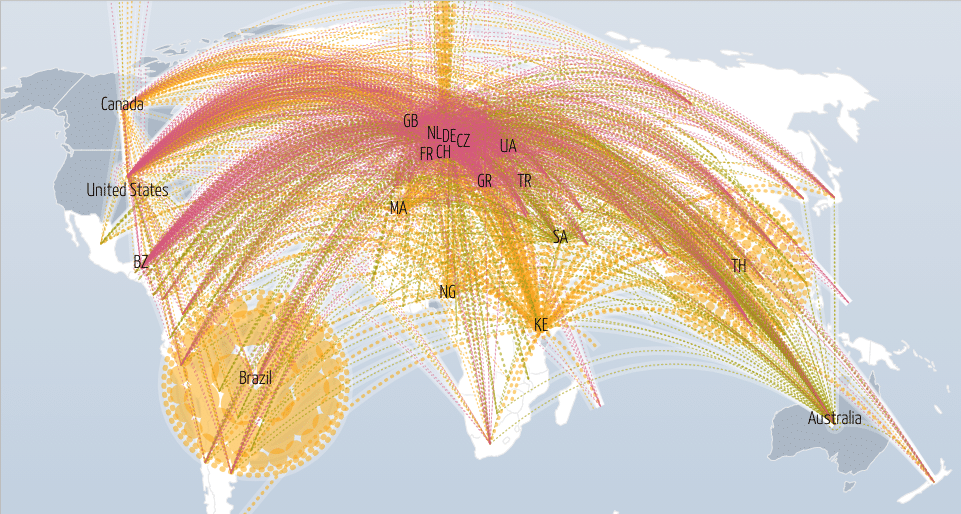
Figure 1: Digital Attack Map
Did you know that every time you’ve gone to see your primary physician or medical specialist that there’s a digital record detailed with what your visit was about and its outcome? This record is known as an EMR (electronic medical record) or EHR (electronic health record)–often referred to interchangeably. It was a revolutionary invention to healthcare because patient information and billing became more centralized and streamlined. In other words, the task of keeping paper records was not only inefficient because it took a lot of time to keep up and store, but it also increased information disparity which information technology has solved. Information is connected now more than ever, and errors are easier to identify. Like all great inventions, there is the unanticipated effect that wasn’t seen coming—the downside of using an EMR is that patient trust remains mixed. The idea of providing personal information handled by at least one human being (or departments of people) you don’t know and technology systems at your doctor’s office or hospital, which you may or may not have access to, challenges human confidence that personal and sensitive information will actually remain completely secure. We start to question computer security and ethics and much more. Patient data is becoming a gold mine for AI research, which is categorized as secondary, and other parties using data to further our understanding of human disease and the future. In this article, we will look at EMR security based on dependability, integrity, and access coupled with countermeasures.
Dependability
Technology dependability means that at any time of the day or night, systems are running as expected 99.9% of the time. Furthermore, every authorized personnel based on his/her/their role may be able to access the system, conduct, and complete transactions on demand. This is critical because data is going through any of the five processes at any given time: transmission, storage, monitoring, algorithmic calculation, and look-ups. If no one can access the system or data isn’t going through the processes which support work continuity at a hospital or medical practice, then there is limited ability to accurately complete a patient encounter and it is now an emergency. The system is down. Data is information. Everything is working around or calling on information.
Athreon’s technology department assesses system dependability and commits to 99.99% up time by going through regular technology audits, continual monitoring, utilizing advanced intelligent software, listening (to systems), enforcing preventative measures, and following company standard protocols to reduce risk and handle downtime events quickly and correctly.
The other facet of dependability is from the patient trust perspective. Often, people don’t trust what they don’t see—or in this case, can’t access. To solve this problem, healthcare organizations have designed their processes and technology to give the access to the patient. However, to what extent patient control can be given will vary and depend. Patients may not be able to alter any information, just view only. This then results in the need to ensure that confidential information is handled right and securely. An empathetic way to look at it is, “Would you protect your information the same way you do mine?”
Integrity and Access
According to Dehling and Sunyaev, integrity requires that information is protected against unauthorized modification or deletion as well as accidental, irrevocable, and undesired changes by authorized users. Data integrity is about maintaining accurate data through consistent processes (in how and who accesses the data as well as how the data is transformed and translated in all technology systems). When data breaches occur, they fall in two types. One being accidental and unintentional, and the other being intentional. For example, a medical professional needs to access and submit a change to an EMR but, in the process, unintentionally accesses more records than he wanted and made a few more changes that he shouldn’t have. He was in a rush to get his task done. This unintentional breach in this example isn’t necessarily about unauthorized access but rather modifying data that now changes everything else downstream. On a nefarious end, another medical professional intentionally breaches the EMR system because they intend to sell personal information in the dark web. How did that happen? He was an employee who won his manager’s confidence very quickly by getting his work done promptly and well. Interestingly, he often pushed to get access to things sooner—and often suggested that protocols were a huge administrative burden that were pointless and not efficient. He’d boast, “Why can’t we just get it done?” Unfortunately, authorization is central to integrity and depending on how sensitive the data is, it will never be instantaneous. Do military and political officials go through background checks in one hour? Hardly.
Athreon upholds integrity in a very robust way, including its system integration efforts. Because trust is central to how technology and its human processes were designed, Athreon offers its clients advanced user management access controls which give clients a clear way of enforcing that everyone has the right access to certain aspects of PII data based on role. Not every role can change data. Some roles are view only. Not every role can extract and download data. Certain roles can authorize. The feature-rich technology offers great complexity in what a user can and cannot do. Likewise, password complexity and administration are rich too and meet the most stringent of audits. Capturing workflow clearly is critical to understand which roles need to do what.
Data Redaction and Cyber Security
Countermeasures designed and implemented to reduce the risk of breaches and handle them expeditiously and correctly will always be a continuous process. When someone or something breaches an EMR system, it endangers EMR security and steals confidentiality. Complex access controls are part of a strong preventative measure to uphold cyber security and trust. Another technology feat Athreon offers is redaction (also referred to as de-identification) on demand. According to NIST, de-identification is a process of concealing data in a certain way so that it reduces linking information revealed in a dataset to specific individuals. This feature is another layer to a robust design that Athreon technology considers to be essential to any strong cyber security policy and program. The less relationships can be determined between data, the better. The pieces of the puzzle for any cyber intruder will remain incomplete. Athreon is also invested in the future, including AI and automatic data redaction, which de-identifies sensitive and personal data (see Figure 2).
Redacted data is not only based on what is seen by the human eye but also what resides in its repositories. And, data also includes metadata which is data about data.

Figure 2: An example of automated data redaction based on recognized personal data.
The Future
Cyber wars and criminal invention will continue. The more interconnected and hyperconnected we are through the internet and our technology devices, the more vulnerabilities we are exposed to—and plenty of data everywhere. EMR security is in a precarious position—it is not just about the right technology but also about the right human processes and controls. Athreon’s expertise not only spans decades in converting speech to text and in technology—it now offers cyber security consulting services. Regardless of industry, if you’d like a one-time complimentary consultation about your business processes, technology designs, and EMR needs–from a current or future perspective–contact us today.